Unless you have been living under a rock, you must have seen businesses falling prey to ever increasing cybercrimes onslaught. Billions of hard earned dollars have been lost, and trillions more are at stake. These are some best practice guidelines to identify email cyber attacks and prevention.
Even though the importance of hardened cyber security infrastructure can’t be over emphasized, knowledge and common sense of the trained end users is equally critical to prevail against cyber exploits. Without further ado let us learn how to identify and prevent common cyber security threats.
Ransomware
Ransomware Definition
Ransomware is a malicious software, which encrypts (locks) the data on the victims network. And, the attacker demands ransom in exchange for unlocking data. Some attackers even threaten to release confidential and/or compromising information to other criminals and public.
Ransomware Attack Methods
- Ransomware may be installed on victim’s computer through an email attachment
- The email may come from a known white listed sender because these known senders might have already been compromised.
- The more sophisticated attacks may even be extremely similar to the ones, which a particular person or department might be expecting. For example, HR may receive a malicious attachment disguised as a resume for a legitimate job opening.
- Ransomware may be unloaded to a computer or network if someone clicks on a malicious AD on a website
- The website itself may be a known good site
- Visiting a malicious website may also compromise a computer and ultimately the entire network
- Again the site itself may be a known good site, but it might have been hacked at that particular moment
Ransomware Prevention
- Implement battle hardened firewalls to protect perimeter. Filter both inbound and outbound traffic
- May also compensate perimeter firewalls with software based firewalls on individual computers
- Responsibility: IT Department
- Keep anti-virus and anti-malware software up to date and run regular scans
- Responsibility: IT Department
- End users must also learn how to confirm that all anti-virus and anti-malware software definition files are up to date. And, if they notice any issues, they must notify their IT Department immediately
- Responsibility: IT Department
- Configure and maintain regular frequent backups
- All of these backups must be encrypted and kept separately from the general network vulnerable to ransomware attacks
- After a successful ransomware attack, secure backups may be the only solution to recover
- The backups should be designed in a way that the complete restores may be performed within minutes. Most companies have the backups, but it may take them hours, weeks or months to restore from them.
- Responsibility: IT Department
- Provide the minimal required access to the network resources. Please note that the malicious actors may only encrypt and lock the data (local and network drives), which is available from the compromised computer and logged in ID.
- Responsibility: IT Department
- Encrypt data both at rest and in transit
- Encrypting data at rest may protect against the threat of exposing confidential and compromising information.
- Responsibility: IT Department
- Educate end users on how to identify and avoid malicious content
- Absolutely never click on a URL or attachment from an unknown sender
- Be extra cautious about opening URLs and attachments from known senders. Ask yourself simple questions such as were you expecting it, does it look legitimate….
- Learn how to identify the actual sender’s address hidden behind the label. Simply hovering over the sender’s name may reveal the actual sender’s address.
- “John Doe – Known Client” <John.Doe.KnownClient@scamer.com>. As in this example, even though “John Doe – Known Client” may look familiar, revealing the underlying address by hovering over it will show the actual scam site.
- And, some of these malicious sites may only have a slight spellings variations to disguise
- “John Doe – Known Client” <John.Doe.KnownClient@scamer.com>. As in this example, even though “John Doe – Known Client” may look familiar, revealing the underlying address by hovering over it will show the actual scam site.
- Don’t click on any advertisements even if they shown on a known good site. Most sites don’t have any control over the shown advertisement.
- Responsibility: End Users
Ransomware Education Additional Resources
Phishing
Phishing Definition
Phishing cyber attacks try to fool you into providing sensitive information. Once a victim provides the sensitive information including credentials, the malicious actors use the information to gain access to the networks, emails, bank accounts as well as sending malicious phishing emails to your unsuspecting trusted contacts on your behalf.
Phishing Attack Methods
- Password reset alerts through emails
- Phishing emails may pretend that you are required to reset your password, and you need to provide your current password to continue. Most of these emails will pretend to be coming from legitimate sources. For example, if your company uses Office 365 email solution, they will pretend to be coming from Microsoft Office 365.
- Voicemails and faxes
- Phishing attacks are also executed through malicious voicemail or faxes alerts. Such voicemail notifications require you to login using your network credentials.
- Requesting personal information updates
- Phishing email may pretend to come from a legitimate business requesting you to update your contact information. They may request your date of birth, social security, contact information and address. Some may even request information such as your bank or credit card account number and pins.
- These phishing scams called vishing may also come through phone calls.
- Phishing attacks called smishing may also come through text messages.
- Some may even hijack your web traffic and redirect to familiar and trusted looking site requesting confidential information. Such attacks are categorized as pharming.
Phishing Prevention
- Most phishing attacks pass through all security parameters undetected because in itself they don’t have any malicious content in terms of infected attachment, code or a URL. They are simple forms and victims practically willingly give away all of the sensitive information.
- Responsibility: End users
- The best and only method to protect against most phishing attacks is to educate end users. Both IT department and end users need to work as a team to develop common sense approach to thwart such phishing attacks.
- Responsibility: IT Department and end users
- Implement multifactor authentication (MFA) to add another layer just in case the passwords are compromised
- Responsibility: IT Department
Phishing Education Additional Resources
Spoofing
Spoofing Definition
Spoofing and phishing go hand in hand. Malicious actors trap by disguising email addresses, sender’s names, phone numbers or website URLs.
Spoofing Attack Methods
- The trick is to make the malicious address look extremely similar to a valid trusted one. Mostly it is a slight spelling or a number variation.
- The spoofed emails may appear coming from a trusted sender. For example, ceo@miraceltechs.com may appear as if it came from a trusted domain miracletechs.com. But, looking closely will reveal a spelling variation of cel instead of cle.
- Spoofed phone numbers may have the same area code and/or rest of the digits as the one of your colleague, family member or even yourself. Or, the caller ID may have a trusted name. Most common spoofed calls pretend to be from IRS or a bank.
- Spoofed URLs either use a spelling variation and/or change the domain suffix. For example, a malicious trusteddomain.net may appear similar to a valid trusted trusteddomain.com. Also, the hyperlink may hide the underlying link. But, hovering over the link may easily reveal the actual URL.
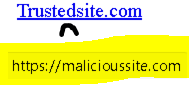
Spoofing Prevention
- Pay close attention to email addresses both the display name and the underlying email address including spellings by hovering over them.
- Responsibility: End users
- Never provide any confidential information over the phone to any unsolicited calls.
- Responsibility: End users
- Don’t blindly click on URLs sent through emails or found through search engines. Always ask yourself why was that URL sent to you, and pay close attention to the underlying URL including its spellings.
- Implement proxy servers to protect against unintentional clicks
- Responsibility: IT Department and End users
- Implement multifactor authentication (MFA) to add another layer just in case the passwords are compromised
- Responsibility: IT Department
Spoofing Education Additional Resources
Malicious Payloads
Malicious Payloads Definition
Malicious payloads come in all shapes and forms. Viruses, malware, spyware, adware, worms, trojan horses, keyloggers among others. Once the victim clicks, downloads, reads or tries to install these malicious payloads, the computer(s) and potentially entire IT infrastructures are immediately compromised. Many of the sophisticated attacks may go unnoticed for months and years. These trained malicious actors open backdoors to mine for additional treasures by quietly capturing credentials and steal business secrets and tricks.
Malicious Payloads Attack Methods
- Hidden inside a legitimate looking document attached to an email
- Through an add on a malicious or even a legitimate site
- Through a URL within body of an email. Most of these malicious URLs are coated with a legitimate looking description
- Link on a website or search engines
- An infected external device such as USB, CD or DVD
Malicious Payloads Prevention
- Trusted enterprise firewalls and email gateways should be used to prevent these malicious payloads from entering the networks.
- Responsibility: IT Department
- Software based firewalls should be installed and configured on all individual computers especially the laptops roaming outside the networks.
- Responsibility: IT Department and End Users
- Setup proxy servers to filter malicious URLs.
- Responsibility: IT Department
- Don’t click on any email attachments unless you are absolutely certain of the content’s legitimacy.
- Responsibility: End Users
- Don’t click on any URLs within an email unless you must and you are certain about its destination. Hover over the URL and confirm that it actually is going to the intended target.
- Responsibility: End Users
- Don’t randomly click on ads and URLs within search engines.
- Responsibility: End Users
- Don’t allow access to personal emails from work computers.
- Responsibility: IT Department and End Users